For Business Cyber Event
& Privacy Liability
When it comes to identifying cyber risks within a business, many are still unfamiliar with what could possibly go wrong,
and the costs and disruptions incurred as a result.
and the costs and disruptions incurred as a result.
As with our reliance on using technology, what we can live with and then live without, you would be excused for thinking that you would
just make do, and the business would try to operate as normal (buy new phones, update servers/hardware, find a new cloud host, etc).
just make do, and the business would try to operate as normal (buy new phones, update servers/hardware, find a new cloud host, etc).
But whether due to an error of judgement or, by not accepting the advice of your MSP to increase your cybersecurity in the first place
(eg. Multi Factor Authentication, Endpoint verification) your business’s ability to stay immune from a cyber-attack, let alone recover in the days,
weeks or years following, depends largely on your ability to control the consequences of a breach.
(eg. Multi Factor Authentication, Endpoint verification) your business’s ability to stay immune from a cyber-attack, let alone recover in the days,
weeks or years following, depends largely on your ability to control the consequences of a breach.
Your MSP understands there are ongoing risks to the businesses they service or why would they be doing what they do?
However, even where you have the best, most reliable MSP in the world and great staff who really understand the technology they use, then ask yourself.
How would I control my business as it weathers a cyber-attack?
While adding layers upon layers of Security to your tech software and hardware is important, arranging Cyber Insurance to safeguard your business and having an Incident Detection & Response plan to know when to report a breach is super important.
This is why we are here in support.
What would it cost NOT to have Cyber Insurance?
Firstly, your MSP understands that by co-ordinating covers through our Cyber Partner Protect program it will provide afforded insurance protection for your business.
What you can then expect is a professional response to a claim that is managed, measured, and resolved so Expenses then arising from a cyber event is not coming out of your hip pocket.
In a worst-case scenario, you should also consider what is most valuable when working with technology: –
- Connecting with other staff or suppliers (via emails, phones, messaging apps)
- Working remotely/ connected to a server to access customer information
- Using banking or supplier software to help manage your business
- Sending off designs, plans, instructions to machinery or to process stock orders in a factory or warehouse.
- Running EFTPOS terminals
- Banking and Accounting - managing yours and clients funds in escrow.
- Tracking staff and contractors for workflow management
By then NOT having a Cyber Insurance plan (not just policy) effectively means that the important relationship between you and your MSP is put under pressure and at that point, we stand by wholeheartedly that the relationship with your MSP must remain strong in the face of a cyber event.
As a business owner, you will know whether you have other uses for technology unique to your business.
Claims expenses can be derived through either Incident Response costs, with the aim of recovering back to normal business operations, as well as costs in the aftermath which could then be Income loss through say losing a customer or potential order, or other costs of Working that are expenses not usually incurred in getting your operations back online sooner than later following a cyber event.
Here is what you can expect to be covered in the event of Cyber Incident
- Incident Response Costs in responding to a cyber incident in real time, including IT security and forensic specialist support, gaining legal advice in relation to ransom demands and breaches of data security.
- Business Interruption Costs in getting your data and applications repaired, restored, or recreated if your computer systems are damaged directly or the systems your suppliers may use that affects the business because of a cyber event
- Data Restoration Costs involved in cleaning out networks and recovering data safely before being placed in a new or its original technology environment for re-use.
- Cyber Extortion Costs associated in negotiating with those looking to expose your data they have been able to access, usually by deceptive means such as social engineering. We politely call these guys “extortionists”. Employees at businesses of all types and sizes may not know what to look out for when it comes to phony links or possible malicious files. Clicking or downloading these can lead to a range of issues including extortion, where hackers threaten to expose data that they’ve accessed, and social engineering, where attackers imitate someone to steal money.
- Third Party (Contingent) Liability Third party claims arising out of a network security or privacy event, be it your transmission of harmful malware to third party systems or failing to prevent the theft of personal data. This typically covers regulatory and PCI fines, penalties and card brand assessments which is particularly important for retail businesses.
- Bodily injury and property damage
- Prior known facts or circumstances Intentional or fraudulent acts
- Damage to computer hardware
- Upgrading of an application, system or network
- Failure or outage of power, utilities, satellites or telecommunication services
SO, what is a Cyber Incident?
is someone or a group that intends to perform malicious actions against
other cyber resources such as your server, laptop, smart phone, a major
supplier, your cloud host, or IT providers managed systems……
other cyber resources such as your server, laptop, smart phone, a major
supplier, your cloud host, or IT providers managed systems……
What is Cyber Insurance?
Covers Financial losses you incur caused by a cyber incident.
Who causes a Cyber Incident?
An adversary that may not care who you are, what information you hold, how much money is in your bank account, only that they want to disrupt your normal operations.
Bit like a vandal, where there is no monetary gain in what they do only that- for a Cyber Hacker it is a mark of respect or notoriety in their world of breaching your Systems, THEY WIN, YOU LOSE!
Who is a cybercriminal, hacker, or adversary?
is someone or a group that intends to perform malicious actions against
other cyber resources such as your server, laptop, smart phone, a major
supplier, your cloud host, or IT providers managed systems……
other cyber resources such as your server, laptop, smart phone, a major
supplier, your cloud host, or IT providers managed systems……
It is an average person (bad actor)
A criminal with intent
A business competitor, enemy or opponent
State actors – who play a role in gaining information control and breaching cybersecurity
A criminal with intent
A business competitor, enemy or opponent
State actors – who play a role in gaining information control and breaching cybersecurity
Incident v Breach
A Breach is because of an event.
Regulatory authorities such as the OAIC through its Privacy Commissioner
have powers to impose a significant fine or penalty based on how you respond
to a matter that involves stolen customer information.
Regulatory authorities such as the OAIC through its Privacy Commissioner
have powers to impose a significant fine or penalty based on how you respond
to a matter that involves stolen customer information.
Breaches, unless proven otherwise, could even be someone purporting to
be the owner or Director sending offensive information to a staff member personally or via social media (Identity Theft).
be the owner or Director sending offensive information to a staff member personally or via social media (Identity Theft).
If you have concerns about the vulnerability of your business to a cyber breach or attack, please talk to us.
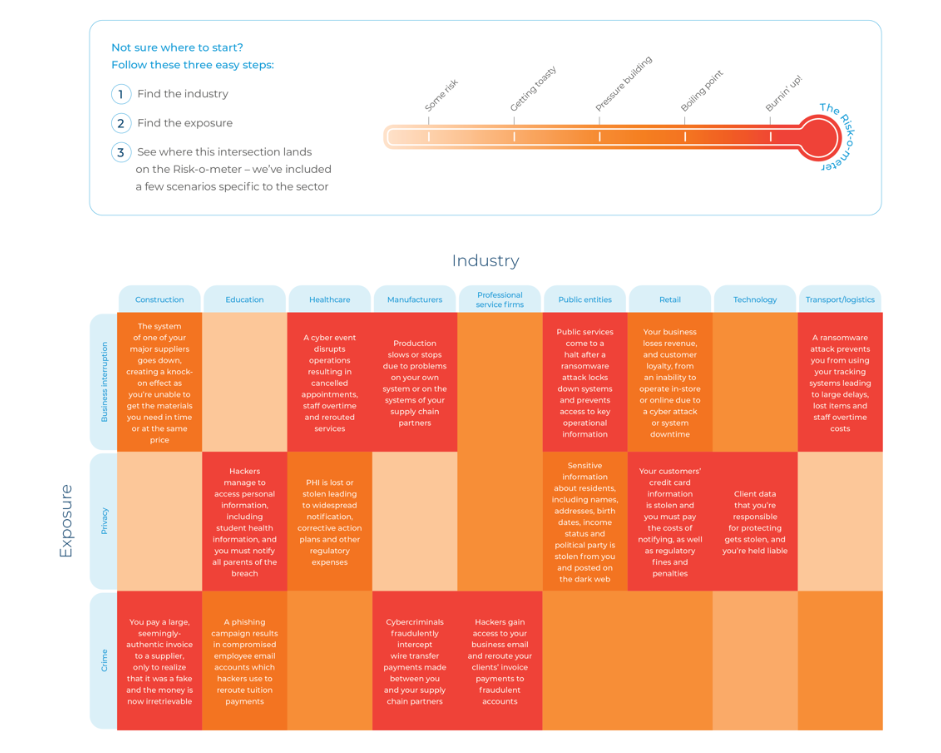
The Cyber risk heat map below (courtesy of CFC Underwriting) was built from over 2,500 claims one of our select underwriters
have dealt with through incident responses.
have dealt with through incident responses.
As a snapshot this offers some examples of different industries’ exposures to business interruption, privacy and cybercrime
that may help as you talk to us.
that may help as you talk to us.
It does not have to be the case of losing control when a cyber event takes hold of your Technology.
But whether by Error or Misfortune we are here in support of: –
PREVENTION , MITIGATION , REMEDIATION
But whether by Error or Misfortune we are here in support of: –
PREVENTION , MITIGATION , REMEDIATION